Mac users who use Ledger hardware wallets to manage their digital assets are being warned about a new scam that uses fake apps to steal funds.
Cybercriminals have launched multiple phishing campaigns using malware that targets macOS systems, replacing the real Ledger Live app with a fake version that asks users to enter their recovery phrase.
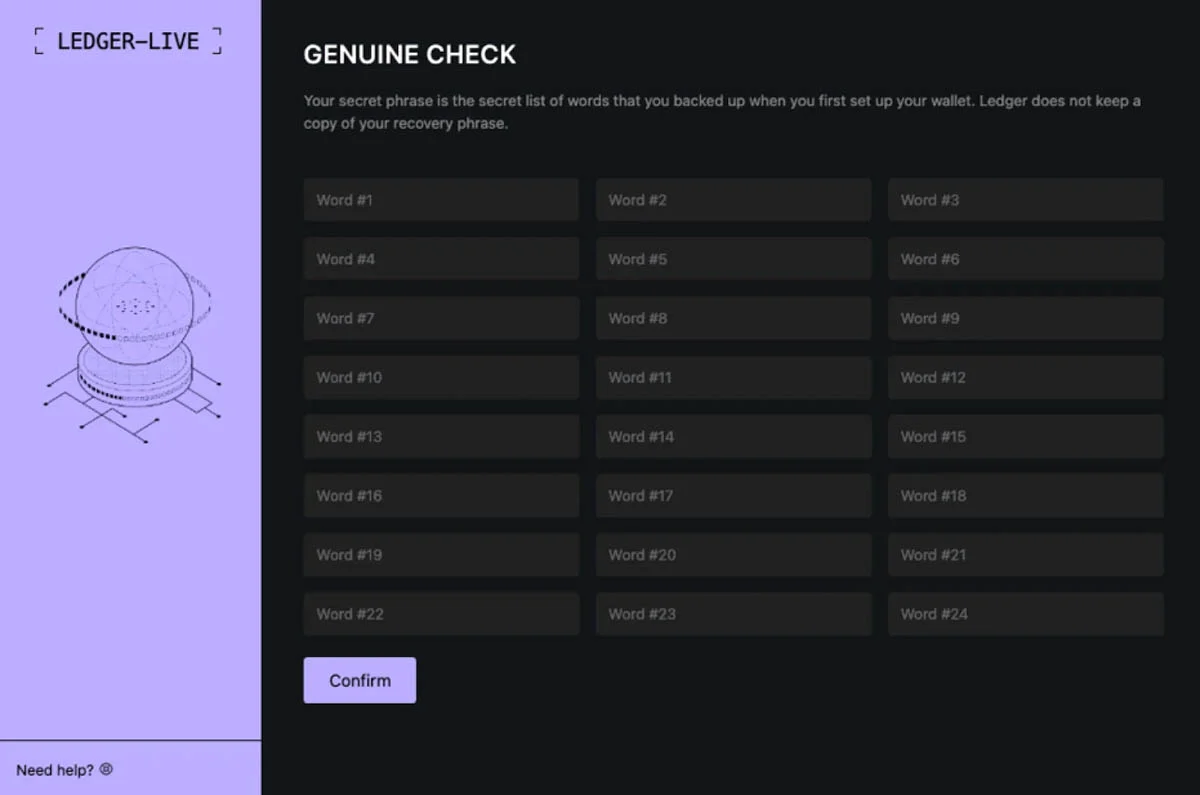
These fake apps look almost identical to the real Ledger Live, but instead of helping users manage their bitcoin, they steal the 24-word recovery phrase—the master key to the user’s digital assets.
According to a detailed analysis by Moonlock, the attacks start when users’ computers get infected with Atomic macOS Stealer malware from one of over 2,800 hacked websites. Once installed, the malware removes the legitimate Ledger Live app and installs a malicious version in its place.
The fake app then shows a pop-up message saying it has detected “suspicious activity”, and asks the user to enter their recovery phrase to fix the issue. Once entered, the seed phrase is sent to a server controlled by the attacker.

“Once entered, the seed phrase is sent to an attacker-controlled server, exposing the user’s assets in seconds,” Moonlock said in their May 22 report.
With the recovery phrase, the scammers can drain the user’s wallet of all digital assets—bitcoin and other tokens.
This isn’t an isolated incident. Moonlock has been tracking this malware since August 2024 and has found at least four active campaigns targeting Mac users. They believe the attackers are getting more sophisticated and are refining their methods.
“This isn’t just a theft. It’s a high-stakes effort to outsmart one of the most trusted tools in the crypto world. And the thieves are not backing down,” Moonlock researchers said.
Initially, the fake Ledger Live apps could only steal passwords and view wallet details. This gave attackers some insight into victims’ assets but no way to steal funds directly.
However, over time, hackers have improved their tactics and are now harvesting recovery phrases, so they can take full control of wallets and move funds freely.
One strain of malware, called Odyssey, was spotted in March and was linked to a hacker using the alias “Rodrigo”.
Odyssey replaces Ledger Live with a trojanized app and displays a phishing page asking users to enter their recovery phrases after showing a fake “critical error” message. Another copycat campaign using AMOS (Atomic macOS Stealer) followed soon after.

In one case, a fake app even displayed an “App corrupted” error after stealing the seed phrase to lower the victim’s suspicion and buy time to transfer the funds.
For years, computers running MacOS were considered safer than their Windows counterparts, because the operating system is less prone to malware. This advanced malware shows that users can never be too careful.
Attackers aren’t just relying on infected apps to steal from users. Other scam tactics include:
- Discord attacks: In May, a moderator account in Ledger’s official Discord server was compromised. Attackers used it to post fake verification links.
- Reddit phishing: In January, a user reported losing $15,000 after unknowingly entering their recovery phrase into a fake app.
- Physical mail scams: In April, some Ledger users received letters claiming to be from the company. These letters included QR codes leading to phishing sites that asked for seed phrases under the guise of a “critical security update”.
Attackers are increasingly targeting users holding hardware wallets, because they might be holding larger amounts.
Earlier this month, a Trezor One user reported being contacted by Coinbase impersonators, who tricked him into entering his seed phrase into a fake website, resulting in loss of 17.5 BTC.
The final goal for all these attacks is similar: the attackers are looking for users’ seed phrases, and they are getting creative in finding new ways to acquire them.
One sure way of staying safe is to learn more. The golden standard rule is to NEVER enter your seed phrase into a computer or a website, no matter how urgent or convincing it looks.
If you are a hardware wallet user, make sure you purchase the wallet from official sources. And the ONLY electronic place you can enter your seed phrases is on the hardware wallet itself.
If a process requires you to enter your seed phrase anywhere on a computer itself, it is definitely a scam.
Related: Bitcoin Hardware Wallet Hacks | What You Need to Know
